Network Modernization – A Practical Guide for Multi-Site Enterprises

Chief Operations Officer
Network Modernization – A Practical Guide for Multi-Site Enterprises
What’s Driving Network Modernization in Multi-Location Enterprises?
The only way businesses can deal with future uncertainty is by investing in human capital and technology infrastructure that can support rapid changes in operating models.
Here are the key reasons why network connectivity and security hence take center stage in any program that aims to build an agile multi-location business.
According to the National Restaurant Association, the restaurant industry is currently operating with a labor shortfall of 540,000 employees. The US Bureau of Labor Statistics reported the annual average total separation rate for the retail industry was 5% compared to 3.9% across all industries in May 2023.
Retail and restaurant operators have to keep a sharp focus on boosting employee productivity at every touchpoint and automating mundane activities. A scalable network backbone is critical to deploy time-saving productivity and collaboration applications and improve application performance.
According to Brandwatch, in 2023, consumers are placing a lot more emphasis on convenience. There is a 12% increase in social media chatter about convenience and shopping experience compared to the previous period.
Restaurant brands have to reimagine the dining space with a focus on enhancing the speed of service, offering greater convenience, and a wide range of digital ordering services. Similarly, retailers have to invest in delivering superior in-store experiences and last-mile fulfillment across channels. None of these are possible without the underlying network and connectivity infrastructure.
The US Department of Agriculture reported that the restaurant consumer price index in July 2023 was 7.1% higher when compared to the same period in 2022. This has impacted both retailers and restaurants. Rising prices also mean unsold inventory. Markdowns and discounts help move them but leave a serious dent in the bottom line.
Retailers and restaurant brands want to streamline every aspect of their operations to cut costs. Economies of scale are needed in the entire supply chain and the underlying tech infrastructure to take advantage of standardized processes. Well-designed network backbones can optimize operating costs and support advanced analytics solutions to streamline the business.
Business locations, especially those in high-risk areas, face significant threats in the form of violent customers, robbery, and gun violence. Internal theft and cash handling risks have historically been a concern for retail and restaurant operators
Retailers and restaurant chains have to invest in intelligent security systems that provide advanced warnings and are capable of zeroing in on anomalies across millions of POS transactions. This requires investment in a wide range of cloud-based, AI-enabled sensors and data analytics. None of these applications can be deployed with outdated network infrastructure.
- Employees are becoming more mobile, accessing the network from various locations and endpoints beyond corporate IT control. They are also connecting to public clouds for essential business applications like Office 365.
- IoT devices, widely distributed in remote and unsupervised locations outnumber human-controlled endpoints opening the door for new security threats.
- Cloud service providers have expanded their presence across numerous branches, which connect directly to the cloud, bypassing corporate data centers.
- With ever-tightening Payment Card Industry (PCI) requirements and data privacy regulations, restaurants and retailers face tremendous risk when migrating data from on-premise POS to cloud-based solutions that offer easier integration with inventory management, online ordering platforms, and the extended supply chain.
- Support for bandwidth-intensive applications such as video management systems and devices with edge computing capabilities that deliver critical real-time data on store operations (such as security cameras) can be challenging when the last-mile connectivity is not properly handled.
The goal of any network modernization program should not only take into consideration the evolving technology solutions that drive transformation but also aim to create a resilient technology operating system that can change rapidly without creating bottlenecks in the future.
Challenges in Managing Legacy Network Infrastructure
There aren’t clear-cut answers. Most likely, retail and restaurant chains always have some part of the network designed decades ago and other parts that were added recently.
Outlets with legacy network components can still run online ordering operations, support in-store applications, and manage their supply chains. The real problem is in administering the network and the penalty it imposes through inefficiencies, downtime, latency, and security vulnerabilities. The limits of what a network infrastructure can support efficiently determine whether a network upgrade is needed or not (Refer to Exhibit 1).
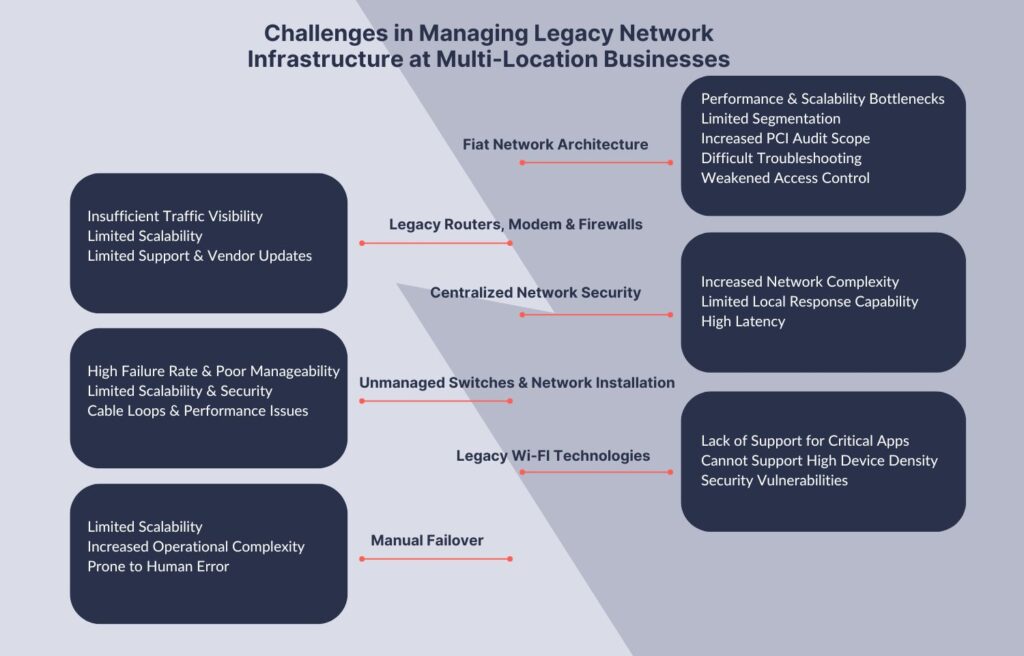
Flat Network Architecture
1. Limited Segmentation
Without dividing the network into security zones, all devices and systems within the organization, such as point-of-sale (POS) systems, employee workstations, and guest networks, are interconnected. This lack of segmentation increases the attack surface, making it easier for an attacker to move laterally across the network. For example, a malware infection in a POS system could spread to the corporate network, compromising sensitive data and systems.2. Increased PCI Audit Scope
In a flat network, the scope of the PCI audit expands, encompassing the entire network infrastructure, rather than just specific segments. This can increase the complexity and cost of compliance efforts.3. Weakened Access Control
Without segmentation, it becomes challenging to implement role-based access controls, network segmentation based on user roles, or least privilege access principles. This can result in unauthorized access to critical resources, data leakage, and a higher risk of insider threats.4. Performance and Scalability Bottlenecks
A flat architecture can hinder performance and scalability. Broadcast and multicast traffic, typically limited to individual segments, can quickly propagate throughout the entire network, leading to congestion, reduced bandwidth availability, and degraded performance.5. Difficult Troubleshooting
Lack of segmentation makes it challenging to pinpoint the root cause of network problems. This results in increased downtime, extended troubleshooting efforts, and potential business disruptions.Manual Failover
1. Limited Scalability
As the network grows in complexity, manually managing failover becomes increasingly challenging. The need for human intervention in every failover event can limit the network’s scalability and agility.2. Increased Operational Complexity
Implementing manual failover requires detailed documentation, well-defined processes, and trained personnel who understand the failover procedures. It also increases the reliance on specific individuals or a limited group of staff members with the necessary expertise.3. Prone to Human Error
There is an increased risk of human error during the transition, such as misconfiguration or oversight, which can lead to service disruptions or unintended consequences. Human error becomes more likely in high-pressure situations, potentially impacting the network’s availability and stability.Centralized Network Security
Some retail and restaurant chains continue to rely on the security infrastructure at the data centers to do the heavy lifting. This approach can stifle application performance and increase network administrative complexities.
1. High Latency
Routing all traffic through the data center for security scans can increase latency and reduce the performance of internet-dependent applications, affecting productivity and user experience.
2. Increased Network Complexity
Implementing a centralized traffic backhauling architecture requires complex network configurations, including routing, load balancing, and secure tunnels to redirect traffic to the data center for security scans. This complexity can make network management and troubleshooting more challenging.
3. Limited Local Response Capability
Backhauling all traffic for security scans to a central data center can limit the ability to respond quickly to local network security incidents. Any network threats or anomalies that require immediate attention or localized mitigation experience delays due to the traffic redirection and the need to wait for security scans performed in the data center.
Legacy Routers, Modems, and Firewalls
1. Insufficient Traffic Visibility
IT teams may struggle to identify and address anomalous or malicious traffic patterns, making it harder to detect and respond to security incidents promptly.2. Limited Scalability
As the network expands with additional branches, devices, and users, legacy routers, modems, and firewalls may struggle to handle the increased traffic volume and advanced security requirements. This can lead to performance issues and network bottlenecks.3. Limited Support and Vendor Updates
Basic routers or consumer-grade firewalls often receive limited vendor support. This can result in outdated firmware, unpatched vulnerabilities, and a higher risk of security incidents due to the lack of ongoing security updates and patches.Unmanaged Switches and Network Installation
1. High Failure Rates & Poor Manageability
Unmanaged switches typically have a lower build quality that can lead to higher failure rates, increased downtime, and the need for frequent replacements.2. Limited Scalability and Security
They lack features such as VLAN support, access control lists (ACLs), or traffic segmentation, which are essential for implementing network security policies and isolating different segments of the network.3. Cable Loops and Performance Issues
Without proper cable management and oversight, unmanaged switches can contribute to cable loops leading to network broadcast storms, increased network congestion, and degraded performance.Legacy WiFi Technologies
1. Lack of Support for Critical Applications
Modern restaurant and retail chains often rely on various advanced applications and technologies like mobile point-of-sale (mPOS) systems, inventory management systems, order management systems, kitchen automation systems, and IoT devices. Legacy WiFi technologies may not offer the necessary capabilities to support these applications efficiently, limiting the potential for digital transformation and innovation.2. Inability to Support High Device Density
As the number of devices connecting to WiFi networks continues to rise, legacy WiFi technologies may struggle to handle the increased device density as they operate on crowded and congested frequency bands, such as 2.4 GHz. This can lead to interference from other devices using the same frequency, resulting in degraded performance and unreliable connections.3. Security Vulnerabilities
Legacy WiFi technologies may lack the advanced security features available in newer standards. This leaves the network more susceptible to unauthorized access, data breaches, and other security threats.How Business Needs Can Be Mapped to Network Modernization
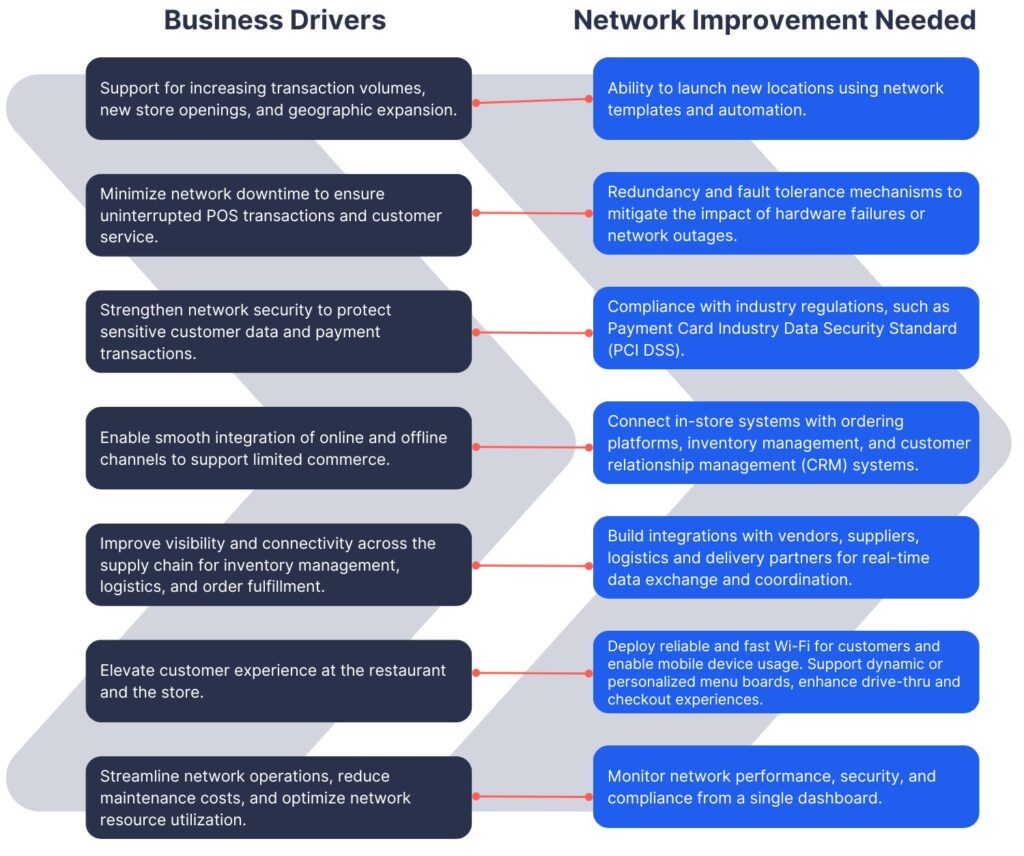
Network Transformation Case Studies
Expand Drive-Thru and Phone Orders for a QSR

Network Requirements
FeastOn IT team identified the need for a high-availability design with 4-hour hardware replacement, WAN failover, redundant 48 port POE switches, 1 access point (guest and company use), VoIP with 4-6 corded phones, loud ringer, caller-ID integration with POS, integration of phones with text messages for order management. They required the ability to deliver drop-free calls during a WAN failure and to keep online orders (web and POS integrators, 60-70% of all orders) working while running on their backup connection. The current POS integration required a single public IP address that could be used over any circuit at each location for this to work.
Solution
FeastOn implemented two different network solutions based on traffic volumes and the growth potential of the location. One set of locations had a 4-hour hardware replacement SLA and the other set of locations came with a high-availability design that did not require immediate hardware replacement. The solution also included a cloud gateway SD-WAN solution that ensured phone calls did not drop during network failure and orders were able to flow seamlessly via the POS integrator that switched to the backup circuit. There were extra redundancy factors added to protect against any cloud gateway failures. This solution provided FeastOn with both WAN and hardware resiliency and met all application and phone failover requirements. This setup allowed them to continue to use some older POS setups while they transitioned to the cloud-based POS in phases.
Eliminate Downtime and Improve Network Security for a Retail Chain

QualityM realized that store operations were always hobbled by patchy network infrastructure nationwide. Network downtime was commonplace, network security management was a headache, and the legacy POTS phone system kept customers unhappy. PCI compliance kept them on their toes because of poor network design.
Network Requirements
QualityM hired a managed network services vendor to come up with a requirement for WAN redundancy, next-day hardware replacement, secure POS traffic, managed next-gen firewall, 24 port switch, two access points (guest and company use), and three cordless phones with an auto attendant that rings a group of phones to place orders.
Solution
The managed services vendor implemented a broadband circuit with automatic failover to an LTE backup. Every store had a single next-gen firewall, a 24 port switch (4 port POE injector used for the APs to keep cost down), and three cordless phones with auto attendant setup. The POS firewall sat behind the next-gen firewall in its security zone. This allowed the POS to use the WAN redundancy setup and still be secure from other network devices, which were separated into four other networks. This network design provided QualityM with a WAN-resilient and secure network.
Thumb Rules for Network Modernization
- Reliability and Redundancy
Design the network to ensure high availability and minimize downtime.
Implement redundant network components such as routers, switches, and firewalls to prevent single points of failure.
Incorporate backup connectivity options, such as failover to secondary circuits or LTE backup, for uninterrupted operations.
- Scalability and Capacity Planning
Design the network to accommodate future growth and increasing network demands.
Consider the scalability of network devices, bandwidth capacity, and network architecture. Plan for potential expansion, new store openings, and increased customer traffic.
- Site Preparation
Conduct a thorough assessment of each store’s infrastructure and requirements. Ensure sufficient power supply, cabling, and physical space for network equipment.
Address any environmental factors that may affect network performance, such as temperature control and ventilation.
- Contracts with Bandwidth Providers
Evaluate and negotiate contracts with bandwidth providers to ensure reliable and cost-effective network connectivity.
Establish Service Level Agreements (SLAs) for uptime, latency, and bandwidth guarantees.
Maintain ongoing communication and relationship management with providers to address any issues or changes.
- Contracts with Hardware Vendors
Assess existing contracts with vendors and hardware providers that are no longer needed.
Plan for a smooth transition to new vendors and hardware, including contract termination and equipment returns.
Ensure proper coordination between the network design and procurement/contract management teams.
- Quality of Service (QoS)
Prioritize critical store applications, like POS (point of sale), inventory management, and sensitive IP traffic.
Allocate appropriate bandwidth and network resources to ensure optimal performance for these applications.
Implement QoS mechanisms to prioritize real-time traffic and minimize latency or packet loss.
- Security
Implement robust network security measures to protect sensitive customer data and maintain PCI DSS (Payment Card Industry Data Security Standard) compliance.
Utilize firewalls, intrusion detection and prevention systems (IDPS), and secure remote access mechanisms.
Apply secure segmentation to isolate critical systems and restrict unauthorized access.
- Bandwidth Optimization
Optimize network bandwidth utilization by leveraging caching, compression, and content delivery networks (CDNs).
Implement traffic shaping and bandwidth management techniques to prioritize business-critical applications and limit non-essential traffic.
- Network Segmentation
Segment the network to enhance security, improve performance, and isolate different store functions.
Separate guest Wi-Fi networks from the corporate network to ensure data confidentiality and prevent unauthorized access.
Segment store operations, point-of-sale, and back-office functions to limit the impact of potential security breaches.
- Wireless Connectivity
Provide reliable and high-performance Wi-Fi connectivity throughout the store premises.
Plan for adequate coverage and capacity to support customer Wi-Fi, mobile devices, and IoT deployments.
Implement secure guest Wi-Fi with captive portals, authentication, and encryption mechanisms.
- Migration and Switchover
Develop a detailed migration plan outlining steps for transitioning from the legacy network to the new infrastructure.
Conduct thorough testing and validation of the new network before the switchover. Plan for minimal disruption to store operations during the migration process.
- Proof of Concept
Roll out a proof of concept (POC) at a limited number of stores to validate the effectiveness of the network design.
Measure the performance, reliability, and security of the new infrastructure in real-world scenarios.
Gather feedback and insights from store staff and IT teams to refine the design before full-scale implementation.
- Monitoring and Management
Implement network monitoring tools to proactively identify and troubleshoot network issues.
Utilize network management systems to centralize network configuration, monitoring, and reporting.
Ensure real-time visibility into network performance, availability, and security events.
- Compliance and Regulatory Considerations
Adhere to industry-specific regulations such as PCI DSS, GDPR, and HIPAA, based on the retail chain’s operations.
Design the network to meet compliance requirements and implement appropriate security controls.
Maintain audit trails, access controls, and security documentation to demonstrate compliance.
- Training
Provide training sessions to educate retail staff on the new network infrastructure and its benefits.
Offer guidance on network usage, security best practices, and troubleshooting common issues.
Ensure that staff members understand how to utilize new applications and tools enabled by the upgraded network.
In-House Vs Managed Services Providers for Network Modernization
- Network Management Skill Gap
The demand for diverse network management skill sets and the ability to hire and retain employees with specialized network engineering skills can be a tough challenge for enterprises who would rather spend the time and money to strengthen core business operations and build products or services.
For example, a medium-sized retail chain or a restaurant chain looking to design and roll out an SD-WAN solution will probably need highly skilled network engineering talent during the initial design and roll-out phase. Once the solution is stable, the IT organization’s focus will be on ongoing maintenance and periodic updates.
- Troubleshooting Challenges in Multi-Vendor Setup
- Limited Geographical Reach
Retail and restaurant chains manage hundreds of geographically dispersed locations or branches. Relying just on internal capabilities and skill sets to manage IT/network operations is not practical for a multi-location enterprise. It’s not feasible for internal network engineers to travel across states or international borders to set up or troubleshoot network issues at branch locations.
- Network Security & Compliance Gaps
In addition to managing a complex security environment, enterprises have to also comply with various data management regulations that are directly related to how secure and compliant the underlying network is. Compliance regulations such as PCI and SOX impose a significant burden on retail IT teams that are focused on complex network modernization challenges. Most retailers face significant cybersecurity challenges as they embrace the cloud and grapple with a combination of lower-than-average staff focused on security operations and inventive cybersecurity attacks that target POS and loyalty management systems.
- Access to Technologies
For a more in-depth understanding of why businesses should hire a managed network services provider, please read this informative blog post.
Your network can be a competitive advantage. Talk to our experts to find out how you can upgrade your network infrastructure and maximize ROI for your investments.
Share this article
About the author

Bud Homeyer
Chief Operations Officer