How Digital Transformation Can Open Doors for Retail Cybersecurity Attacks

SVP, Engineering
How Digital Transformation Can Open Doors for Retail Cybersecurity Attacks
60%
Retailers are Investing in Digital Transformation
retailers have either implemented digital transformation initiatives or are in the process of implementing digital transformation projects.60% Retailers are Investing in Digital Transformation
retailers have either implemented digital transformation initiatives or are in the process of implementing digital transformation projects.Primary focus of
digital transformation
digital transformation
Retailers’ data lakes are attractive targets, often combining detailed identity and demographic data with credit card information.
percent of consumers are confident that retailers will be able to navigate the challenges of a data breach
Retailers are apparently more likely to pay off ransomware attackers. Of those that experienced such an attack, 51% paid the ransom directly (versus 37% of their peers in other industries).
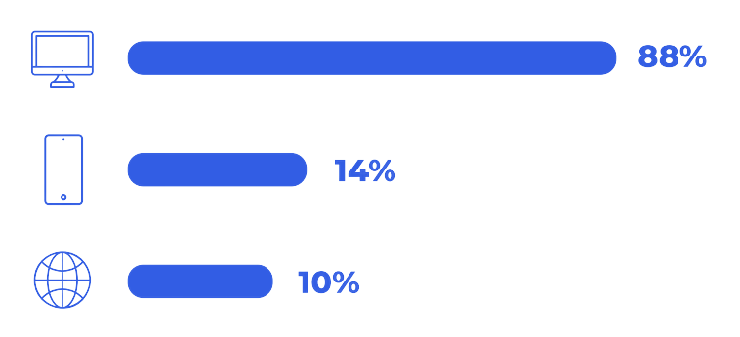
Retailers surveyed tend to have smaller SOCs than their peers
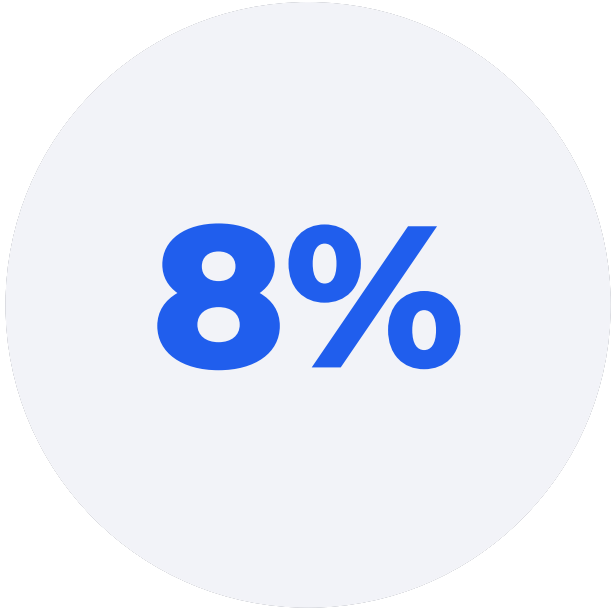
report that their SOC consists of more than 50 FTEs (versus 20% of SOCs across industries).
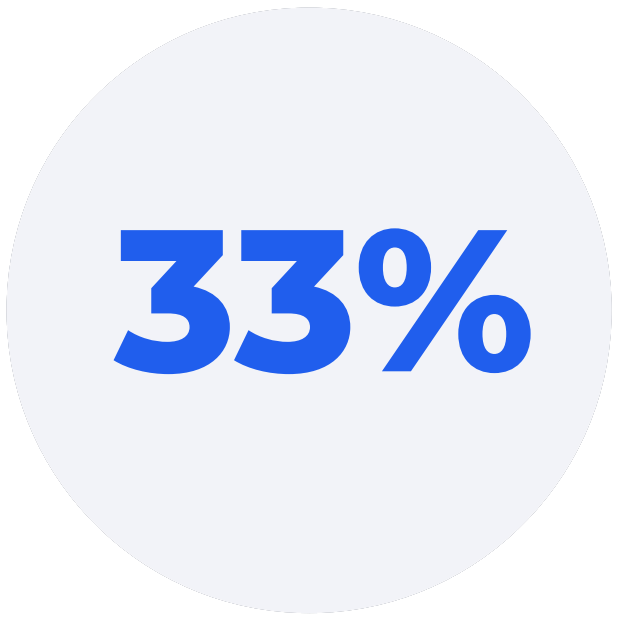
say the cybersecurity team being understaffed for the size of their organization is a top challenge (versus 25% across other industries).
4
Four basic security
policies are needed for
today's enterprise
01
Restrict access to data on a need-to-know basis.
02
Encrypt sensitive data sent across open public network.
03
Regularly test security systems and processes
04
Change all default, vendor supplied processes
14% of organizations complied with all four requirements in 2018
Only 9% of organizations complied with all four requirements in 2021
Retail Cybersecurity Threats Targets , Actors & Implications
Targets
84%
attacks include one of the following –
System Intrusion, Social Engineering, Basic Web Application attacks
Threat actors
87%
External actors
13%
Internal actors
Retail Cybersecurity Threats Targets , Actors & Implications
Retailers are betting big on enabling employees to work from anywhere. Convenience is now offered in the form of:
- BYOPC (Bring Your Own PC)
- BYOD (Bring Your Own Device)
- CYOD (Choose Your Own Device)
- COPE (Company Owned Personally Enabled)
- COBO (Company Owned Business Only)
40%
respondents said mobile devices are their company’s biggest IT security threat
31%
respondents agreed that mobile device threats were growing faster than other threats.
How Can Retailers Secure Mobile Devices?
- Define a BYOD and WFM policy
- Implement Mobile Device Management (MDM) solutions
- Implement Endpoint Detection and Response (EDR) solutions
- Implement Data Loss Prevention (DLP) solutions
- Implement Mobile Threat Defense (MTD) and Unified Endpoint Management (UEM)
- Provide adequate training to employees and IT teams
Cybercriminals Are Checking Out POS
Adoption of self checkout use cases is expected to increase from a relatively low 15 to 35 percent of organized retail today to 80 to 90 percent in 2030.
In store purchases are vulnerable to fraudulent purchases according to 49.3% of retailers. Multichannel purchases (bought online and picked up in store) are vulnerable to fraudulent activities according to 18.8% of retailers. (NRF, 2020)
POS applications are directly connected to credit card data, loyalty management applications, and inventory management systems. They are easily accessible to anyone and retailers struggle to manage the sheer number of in store terminals, self service kiosks, mobile payment devices, and phone based payments directly from customers.
62%
attacks on POS environments are completed through remote access.
Scamsters rely on shimming and man in the middle (MITM) attacks to impersonate EMV credit cards at the POS.
In 2019, an employee clicked on a malicious link in a phishing email and downloaded a Remote Access Trojan. The attackers used the Trojan to move laterally into the merchant's PoS environment where they deployed a RAM memory scraper for harvesting payment card data.
Data Breaches are Expensive
$ 3.28 M
is retail industry’s average cost of a data breach (IBM Cost of Data Breach Report, 2022)
How Can Retailers Secure POS?
- Encrypt all POS data end to end
- Implement EMV and NFC technologies
- Whitelist applications to run on a POS system
- Keep your POS software up to date
- Segment the POS network
- Address PCI DSS compliance gaps proactively
- Physically secure POS devices including mobile POS devices
- Watch out for unusual transactions
- Integrate security camera with POS transactions
Cyberattacks on the Cloud
50% of retailers surveyed have a cloud first policy for new applications compared to 38% of organizations across other verticals.
Cloud misconfiguration accounted for 15% of the breaches and costs the company $4.14 million on average.
Malware targeting Linux environments rose dramatically in 2021—a surge possibly correlated to more organizations moving into cloud based environments, many of which rely on Linux for their operations.
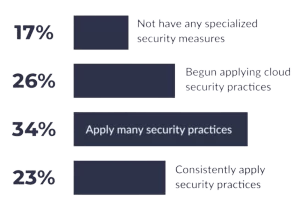
Cloud Security Maturity
Sky High Cost of Cloud Security Breaches
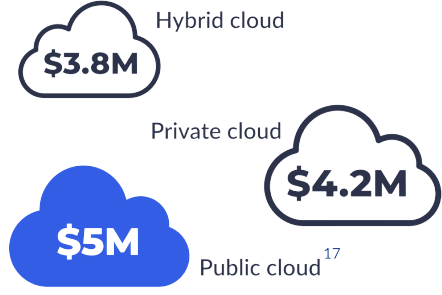
How Can Retailers Secure the Cloud?
- Adopt a zero trust security model to help prevent unauthorized access to sensitive data
- Protect sensitive data in cloud environments using policy and encryption
- Understand the scope of cloud service provider security responsibilities
- Organize ongoing security awareness training for all employees
- Invest in security orchestration and automation of response (SOAR) and extended detection and response (XDR) to help improve detection and response times
Loyalty Programs and Gift Cards
22%
consumers shop exclusively with retailers to take advantage of loyalty programs.
$140 billion
Estimated value of loyalty points in the US
$100 billion
Estimated value of rewards that go unclaimed
$ 259B by 2026
The gift card market in the US will increase from US$172 billion in 2021 to reach US$259 billion by 2026.
number of gift card
cyberattacks when compared
to other targets
Impact of Loyalty and Gift Card Fraud
01
Estimated value of rewards fraudulently redeemed each year $1 billion
02
The FTC estimates an based on 64,000 consumer complaints that amount to a collective loss of $233 million.
03
Any data breach involving loyalty management applications could potentially attract regulatory fines under the provisions of the California Consumer Privacy Act (CCPA) and GDPR
Loyalty account takeover fraud is a ticking timebomb. According to Forter, As fraudsters accrue more account data during this period, merchants should remain vigilant. Fraudsters are breaching accounts and stealing personal data, using this time to age the accounts they steal. They are taking the time to build the account’s reputation, making it more difficult for rules based systems or manual review teams to detect a hacked account from a legitimate one.
How Can Retailers Minimize Loyalty and Gift Card Frauds?
Implement a robust data analytics system to flag suspicious transactions.
Enforce password policies and encouragemultifactor authentication.
Limit the personal data needed to enroll in therewards program.
Regulate access to loyalty managementsystems and implement a zero trust securityframework.
Accelerate Retail Digital Transformation with Interface
PCI-compliant LAN, WAN, Firewall, SD WAN, and VoIP in one standardized package
Turnkey network-as a service to deliver network security and optimal performance
Unified ZTNA, FWaaS, SWG & SD-WAN solution
Interface simplifies PCI compliance for businesses
3.Verizon Mobile Security Index 2021
4.Fiserv
5. https://www.splunk.com/en_us/form/state of security/thanks.html
6. https://www.splunk.com/en_us/form/state of security/thanks.html
7.2022 Verizon Data Breach Investigations Report
8. https://www.verizon.com/business/resources/reports/mobile security-index/
10. https://www.akamai.com/blog/security/understanding point of sale security
12. https://www.experian.com/blogs/ask-experian/what is an emv chip/
13. https://www.splunk.com/en_us/form/state of security/thanks.html
14. https://www.ibm.com/security/data breach/threat intelligence/
15.IBM Cost of Data Breach Report 2022
16. https://www.globenewswire.com/en/news release/2022/03/23/2408637/28124/en/United-States Gift Card and-Incentive Card-Market Report 2022
Market is-Expected to Grow by-9 5 to Reach 188 832 7 Million in 2022 Forecast to 2026.html
About the author

Steve Womer
SVP, Engineering